Updating this question to reorganize relevant information:
I’ve downloaded the MSI installer, ver. 6.3.4, for Windows 10 (64bit), as well as the keys and offline help installer from the LibreOffice downloads page.
- Windows MSI installer file size matches what is stated on the downloads page.
- The MSI hashes match:
“>certutil -hashfile LibreOffice_6.3.4_Win_x64.msi sha256
SHA256 hash of LibreOffice_6.3.4_Win_x64.msi:
94b2b86b5688685233479d594e5760ce24d5b9a00e33058f4b86dffd08b54574
CertUtil: -hashfile command completed successfully.”
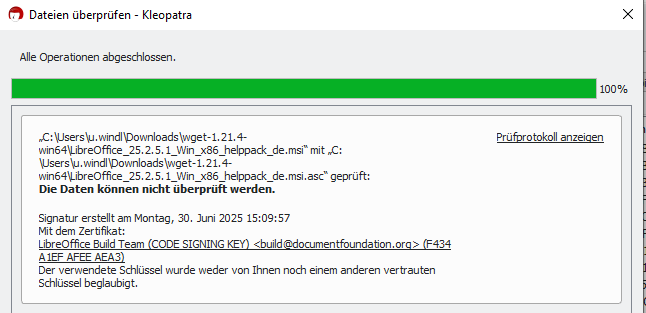
My question is, how do I verify the integrity of the keys before importing them (so that I can verify the download using gpg)? I expected to find some reference to the output I should see once I verified the file. I could not find anything saying what I should expect; I’ve searched through a variety of sources including Googling the RSA key, but no luck:
This was my output prior to importing the key (I forgot to do that before verifying, sorry)
“>gpg --verify LibreOffice_6.3.4_Win_x64.msi.asc LibreOffice_6.3.4_Win_x64.msi
gpg: Signature made 12/10/19 05:32:29 Eastern Standard Time
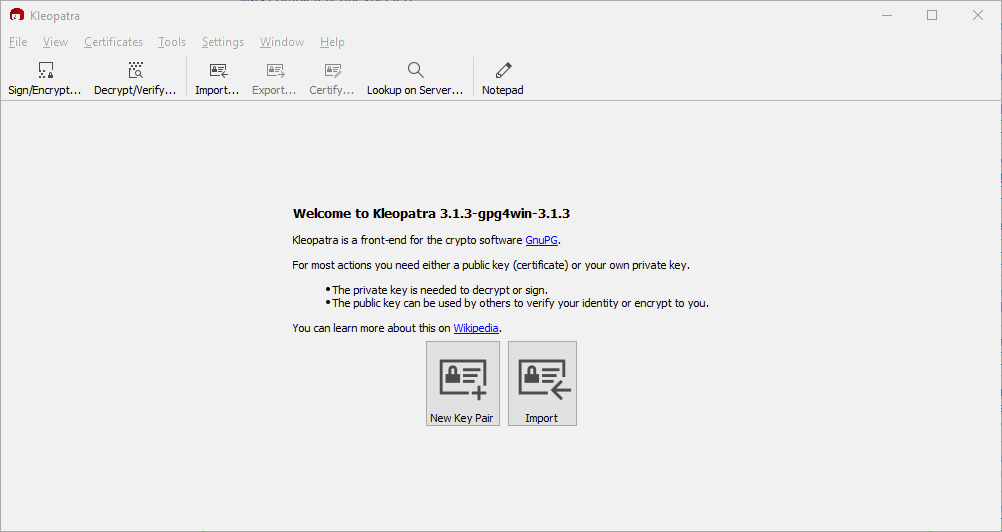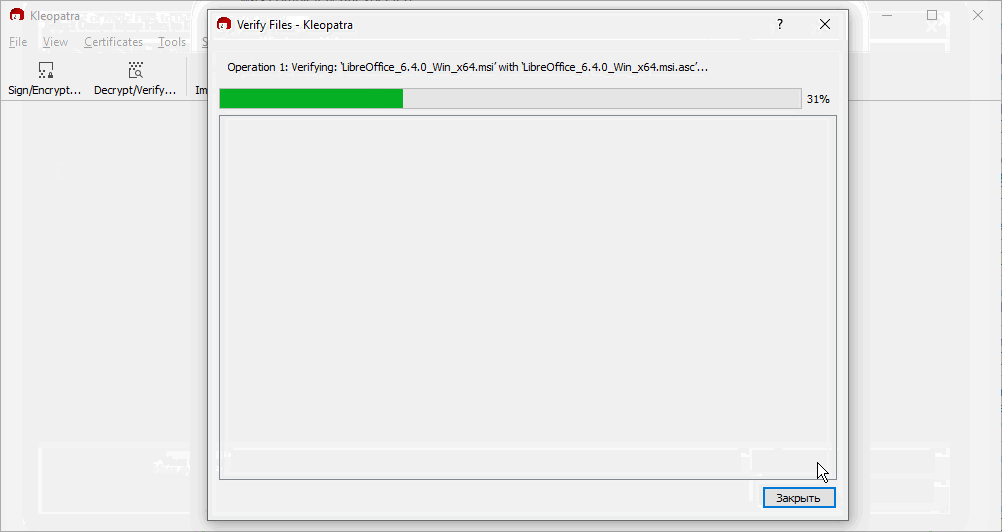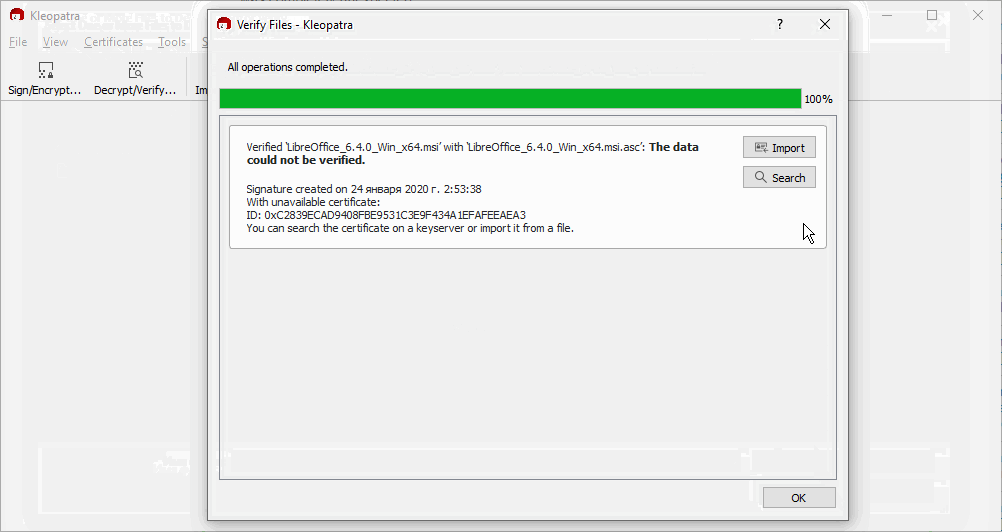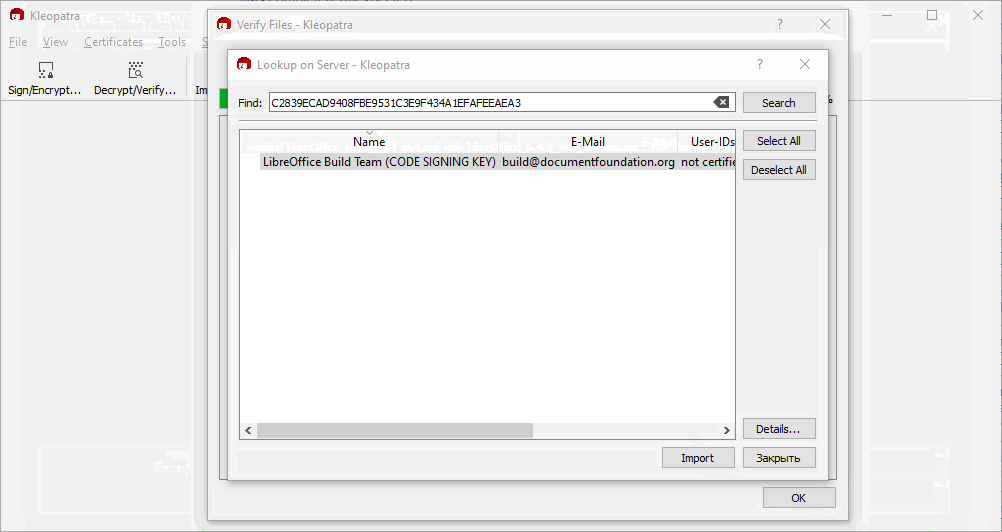
gpg: using RSA key C2839ECAD9408FBE9531C3E9F434A1EFAFEEAEA3
gpg: Can’t check signature: No public key”
This was my output after importing it (which is what I was expecting)
">gpg --verify LibreOffice_6.3.4_Win_x64.msi.asc LibreOffice_6.3.4_Win_x64.msi
gpg: Signature made 12/10/19 05:32:29 Eastern Standard Time
gpg: using RSA key C2839ECAD9408FBE9531C3E9F434A1EFAFEEAEA3
gpg: Good signature from “LibreOffice Build Team (CODE SIGNING KEY) build@documentfoundation.org [unknown]
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: C283 9ECA D940 8FBE 9531 C3E9 F434 A1EF AFEE AEA3”
I know that my question may seem unecessarily pedantic, but how do I verify the integrity of the RSA key if the host doesn’t provide some reference to what I expect? For example, some sites may say something like “the key will end in F434 A1EF AFEE AEA3” but I can’t seem to find anything. How do I know the key is authentic?